Researchers from the cybersecurity company, SentinelOne have discovered that Microsofts Windows Defender is being abused by a threat actor associated with the LockBit 3.0 ransomware operation to load Cobalt Strike beacons onto potentially compromised systems and evade EDR and AV detection tools.
The researchers found that Microsoft Defenders command line tool MpCmdRun.exe was abused to side-load malicious DLLs that decrypt and install Cobalt Strike beacons on victims PCs.
For those unaware, MpCmdRun is an important part of Microsofts Windows Security system that helps protect your PC from online threats and malware.

During a recent investigation, we found that threat actors were abusing the Windows Defender command line tool MpCmdRun.exe to decrypt and load Cobalt Strike payloads, SentinelOnewrotein detail about the new attack in its blog post.
The initial target compromise in both cases occurred by exploiting theLog4j vulnerabilityagainst an unpatched VMWare Horizon Server to run PowerShell code, which downloaded the MpCmdRun.exe, the mpclient malicious DLL file, and the encrypted Cobalt Strike payload file from its Command-and-Control (C2) server.
The threat actor downloads a malicious DLL, the encrypted payload, and the legitimate tool from their controlled C2:
Notably, the threat actor leverages the legitimate Windows Defender command line toolMpCmdRun.exeto decrypt and load Cobalt Strike payloads.
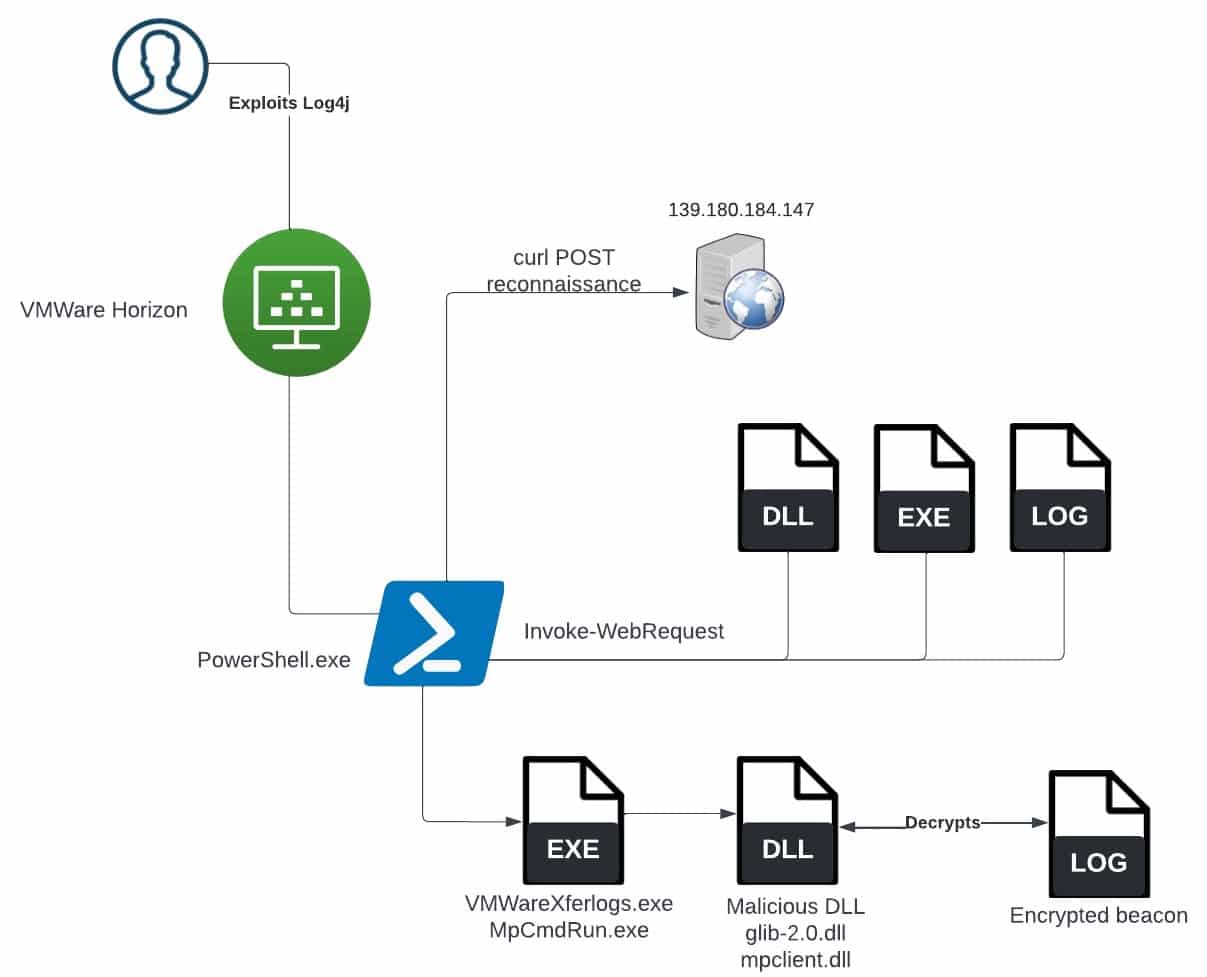
[…]MpCmd.exe(sic) is abused to side-load a weaponizedmpclient.dll, which loads and decrypts Cobalt Strike Beacon from the c0000015.log file.
As such, the components used in the attack specifically related to the use of the Windows Defender command line tool are:
For more technical details, it’s possible for you to check out the officialblog post here.
Read More

source: www.techworm.net